Hill Cipher is a polygraphic substitution cipher based on linear algebra. Each letter is represented by a number modulo 26. Often the simple scheme A = 0, B = 1, Z = 25 is used. Get program for caesar cipher in C and C for encryption and decryption. What is Caesar Cipher? It is one of the simplest encryption technique in which each character in plain text is replaced by a character some fixed number of positions down to it.
Hill Cipher Program Source Code Example
- Related Questions & Answers
- Selected Reading
Vigenere Cipher is a kind of polyalphabetic substitution method of encrypting alphabetic text.
Vigenere Cipher Table is used in which alphabets from A to Z are written in 26 rows, for encryption and decryption in this method.
Encryption
Key: WELCOME
Message: Thisistutorialspoint
Here we have to obtain a key by repeating the given key till its length becomes equal to original message length.
For encryption take first letter of message and key i.e. T and W. Take the alphabet in Vigenere Cipher Table where T row and W column coincides i.e. P.
Repeat the same process for all remaining alphabets in message text.
Finally, the encrypted message text is −
Encrypted Message: PLTUWEXQXZTWMPOTZKBF.
The cipher text can be generated by below equation.
Ei = (Pi + Ki) mod 26
Here P is plain text and K is key.
Decryption
Key: WELCOME
Encrypted Message: PLTUWEXQXZTWMPOTZKBF
Take generated key and first alphabet of encrypted message i.e. P and W. Analyze Vigenere Cipher Table, look for alphabet P in column W, the corresponding row will be the first alphabet of original message i.e. T.
Repeat this process for all the alphabets in encrypted message.
Original Message: Thisistutorialspoint
This can be represented in algebraic form by following equation.
Pi = (Ei – Ki + 26) mod 26
Here is a C++ program to implement Vigenere cipher.
Algorithms
Example
Output
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a procedure. An alternative, less common term is encipherment. To encipher or encode is to convert information into cipher or code. In common parlance, 'cipher' is synonymous with 'code', as they are both a set of steps that encrypt a message; however, the concepts are distinct in cryptography, especially classical cryptography.
Codes generally substitute different length strings of character in the output, while ciphers generally substitute the same number of characters as are input. There are exceptions and some cipher systems may use slightly more, or fewer, characters when output versus the number that was input.
In this post, we will discuss the Playfair Cipher. The Playfair cipher is a cryptographic technique that is used to encrypt/decrypt a message. The technique encrypts pairs of letters (bigrams or digrams), instead of single letters as in the simple substitution cipher and rather more complex Vigenère cipher systems then in use.
Working
The Playfair cipher uses a 5 by 5 table of letters. To generate the key, we will first fill the table row-wise with the letters of the key. We omit the repeating letters. After this, we fill the table with the remaining letters. We usually omit the letter i or j so that the number of letters in the table is 25. After the table is generated, we divide the message into the pairs of 2. Then for each pair, we look up the position of the letters in the table. Suppose the pair is XY and X is at position (x1,y1) and Y is at position (x2,y2), we choose the letters which are at position (x2,y1) and (x1,y2). If the pairs are (x,y1) and (x,y2), then we choose the letters at (x,y1+1) and (x,y2+1).
If the pairs are (x1,y) and (x2,y), then we choose the letters at (x1+1,y) and (x2+1,y).
For example, if the message is 'helloworld' and the key is 'test'. Download game god of war di ppsspp. We will generate the following table:
The original message and the encrypted message will be:
We will use C++ to write this algorithm due to the standard template library support. Hence, we will write the program of the Playfair Cipher algorithm in C++, although, it's very similar to C.
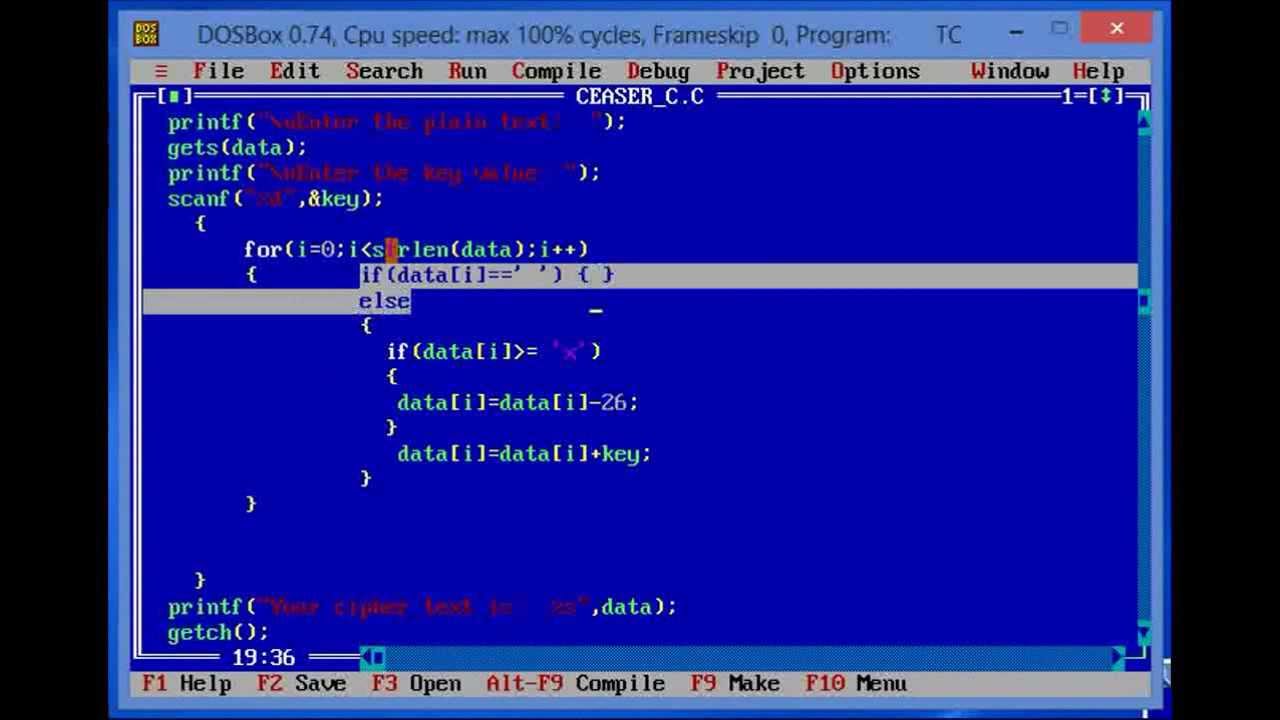
Encryption
INPUT:
line 1: message
line 2: key
OUTPUT:
line 1: Encrypted message
The following is the Playfair Cipher encryption algorithm program in C++.
OUTPUT:
Decryption
INPUT:
line 1: message
line 2: key
OUTPUT:
line 1: decrypted message
The following is the Playfair Cipher decryption algorithm program in C++.
OUTPUT:
Hill Cipher Program Source Codes
Other cryptography algorithms:
Let us know in the comments if you are having any questions regarding this cryptography cipher Algorithm.
And if you found this post helpful, then please help us by sharing this post with your friends. Thank You
